Is section 5101 loophole bank income email offer a scam raises critical questions regarding the legitimacy and potential risks associated with unsolicited financial propositions received via email. This examination delves into the deceptive tactics employed by fraudulent schemes, aiming to equip individuals with the knowledge necessary to discern genuine opportunities from predatory offers.
These email solicitations often present themselves as avenues to financial gain through obscure “loopholes,” frequently referencing obscure sections of tax codes or financial regulations, such as Section 5101. They commonly promise substantial returns or tax advantages with minimal effort, preying on individuals’ desires for financial security or increased wealth. The primary parties involved typically include the sender of the email, who acts as an intermediary or promoter, and the recipient, who is the target of the potential scam.
Understanding the initial appeal and the underlying mechanics of these offers is the first step in identifying their true nature.
Understanding the Core Offer

The digital landscape is often fertile ground for innovative financial opportunities, yet it also presents pathways for sophisticated schemes. Among these, “Section 5101 loophole bank income email offers” have emerged, piquing curiosity and, for many, raising significant red flags. These solicitations promise access to unique financial benefits by leveraging a purported “loophole” within Section 5101 of a relevant tax code or banking regulation.
The allure lies in the suggestion of a readily available, underutilized mechanism for generating income or financial advantages that has been overlooked by the general public.At its heart, the core offer of these emails revolves around an implied secret or exclusive knowledge. They present themselves as conduits to financial enrichment, often by suggesting that by following their instructions or engaging with their service, individuals can tap into previously inaccessible funds or benefits.
The language employed is typically designed to sound authoritative and complex, hinting at intricate financial or legal processes that are being simplified for the recipient. This complexity is often a deliberate tactic to obscure the lack of genuine substance in the offer.
Typical Appearance of Legitimacy
These offers frequently employ several strategies to appear credible. They may use professional-looking email templates, mimic official government or financial institution branding, and incorporate jargon that sounds official. The promises are often framed in terms of tax refunds, unclaimed funds, or special investment opportunities, tapping into common desires for financial security and growth.
Common Promises and Advertised Benefits
The advertised benefits in these email solicitations are varied but consistently target financial gains. Common promises include:
- Significant tax refunds or credits that were previously unclaimable.
- Access to dormant or unclaimed bank accounts and funds.
- Guaranteed high returns on investments with minimal risk.
- Eligibility for special government grants or financial assistance programs not widely known.
- Opportunities to reduce or eliminate tax liabilities through obscure legal interpretations.
Primary Parties Involved
The typical transaction structure for these “Section 5101 loophole bank income email offers” involves several key parties:
- The Sender/Promoter: This is the entity or individual behind the email offer, presenting themselves as experts or facilitators of the supposed loophole. They are the ones who guide the recipient through the process and usually request some form of payment or personal information.
- The Recipient/Victim: This is the individual who receives the email and is enticed by the offer. They are the target for the promoter’s scheme.
- Potentially, Fictitious or Compromised Institutions: In some instances, these offers might reference or impersonate legitimate financial institutions or government agencies to lend an air of authenticity. It is crucial to understand that these entities are often not genuinely involved but are used as a facade.
Identifying Potential Red Flags: Is Section 5101 Loophole Bank Income Email Offer A Scam

As we navigate the often-murky waters of financial offers, particularly those promising unconventional avenues for income, vigilance becomes our most potent shield. Recognizing the subtle, and sometimes not-so-subtle, indicators of a potential scam is paramount to safeguarding our hard-earned resources and peace of mind. These warning signs are not arbitrary; they are the tell-tale footprints left by those who seek to exploit trust for illicit gain.These deceptive schemes often employ a playbook of manipulation, preying on the desire for financial ease and security.
By understanding their common tactics, we can better equip ourselves to discern genuine opportunities from fabricated ones, ensuring our financial journey remains on a path of integrity and sound decision-making.
Common Warning Signs in Email Offers
When an email lands in your inbox promising extraordinary financial benefits, especially those referencing obscure tax codes or loopholes, a healthy dose of skepticism is warranted. These offers are frequently designed to bypass standard financial due diligence by appealing to a sense of urgency and exclusivity.The following are common indicators that an email offer might be a scam:
- Unsolicited Nature: The offer arrives unexpectedly, without any prior interaction or request from your end. Legitimate financial institutions or advisors typically build relationships before presenting tailored opportunities.
- Vague or Overly Complex Explanations: The details of how the “loophole” works are either unclear, filled with jargon that is difficult to understand, or rely on extremely niche and obscure interpretations of financial regulations.
- Guaranteed High Returns with Little to No Risk: Any investment or financial strategy that promises exceptionally high returns with absolute certainty and no accompanying risk is a significant red flag. Real-world financial opportunities always involve some level of risk.
- Pressure to Act Immediately: Scammers often create a false sense of urgency, compelling recipients to act quickly before they have time to thoroughly research or consult with trusted advisors. Phrases like “limited time offer” or “act now before it’s too late” are common.
- Requests for Upfront Fees for “Access” or “Processing”: While legitimate services may have fees, being asked to pay a substantial fee upfront to access information about a loophole or to process a supposed refund is highly suspicious.
- Poor Grammar and Spelling: While not definitive, many scam emails contain numerous grammatical errors and spelling mistakes, indicating a lack of professionalism and attention to detail that is uncharacteristic of legitimate financial communication.
- Lack of Verifiable Contact Information: The email may provide only a generic email address or a non-functional website, making it difficult or impossible to verify the legitimacy of the sender or their organization.
Types of Personal Information Requested
A primary objective of many scams is to obtain personal information that can be used for identity theft, financial fraud, or further phishing attempts. Legitimate financial institutions have strict protocols for requesting sensitive data, and these requests are typically made through secure channels and only after a verified relationship has been established.Suspicious entities often request a broad range of personal information, including but not limited to:
- Social Security Number (SSN): This is a highly sensitive piece of information that, if compromised, can lead to significant financial identity theft.
- Bank Account Numbers and Routing Information: Providing these details without a clear and verified purpose can allow scammers to initiate fraudulent transactions or drain accounts.
- Credit Card Numbers: Similar to bank account information, this can be used for unauthorized purchases.
- Date of Birth: Often used in conjunction with other pieces of information to impersonate individuals.
- Mother’s Maiden Name: A common security question used by financial institutions, making it a prime target for scammers.
- Login Credentials for Online Accounts: This includes usernames and passwords for banking, email, or other sensitive online services.
- Copies of Identification Documents: While some legitimate processes might require verification, unsolicited requests for scanned copies of passports or driver’s licenses are highly suspect.
Unusual Payment Methods or Fees
The methods by which a scammer requests payment are often as telling as the initial offer itself. Legitimate financial transactions typically involve standard, traceable methods. Deviations from these norms are designed to make it difficult to recover funds and to obscure the identity of the perpetrators.Examine these unusual payment methods and fee structures carefully:
- Payment via Gift Cards: Demanding payment in the form of gift cards (e.g., Amazon, Apple, Google Play) is a classic scam tactic. These payments are virtually untraceable and irreversible.
- Wire Transfers to Unfamiliar Individuals or Businesses: While wire transfers are legitimate, being asked to send money to an individual or an obscure overseas business, especially for an unsecured “opportunity,” is a major warning sign.
- Cryptocurrency Payments for Unverified Services: While cryptocurrency is a legitimate asset, its pseudonymous nature can be exploited by scammers. Being pressured to pay fees or invest using cryptocurrencies for an unverified offer is highly risky.
- Prepaid Debit Cards: Similar to gift cards, prepaid debit cards can be used to make payments that are difficult to trace.
- Upfront “Processing Fees” or “Insurance Fees” for Refunds or Benefits: Scammers often claim you need to pay a fee to unlock your promised funds, such as a tax refund or a settlement. These fees are designed to extract money without any intention of providing the promised benefit.
- Requests for Payment to a “Holding Account” or “Escrow Service” Not Recognized by Reputable Financial Bodies: Be wary of any mention of obscure or unverified holding accounts.
Examples of Vague or Overly Aggressive Language
The language used in scam emails is often crafted to manipulate emotions and bypass rational thought. It can be characterized by a blend of ambiguity and forceful persuasion, designed to create a sense of urgency and desirability.Here are examples of the types of language commonly found in such communications:
- Vague Promises: “Unlock hidden assets,” “claim your unclaimed funds,” “access exclusive tax benefits,” “repatriate offshore capital.” These phrases lack specificity and do not explain the mechanism by which these benefits are achieved.
- Overly Technical or Jargon-Filled Language: Employing complex financial or legal terms without clear explanation, often to intimidate or impress the recipient into believing the offer is legitimate and beyond their understanding. For instance, referencing non-existent sections of tax codes or convoluted financial instruments.
- Urgency and Scarcity Tactics: “This opportunity will not last,” “Act now to secure your refund,” “Limited spots available,” “Government regulations are changing, you must act immediately.” These phrases are designed to prevent careful consideration.
- Authoritative but Unverifiable Claims: “As per the latest directive from the International Revenue Service (IRS) –
-note: this is a fabricated claim, the IRS does not operate this way* – you are eligible for a one-time refund.” Scammers often impersonate legitimate organizations. - Emotional Appeals: “Don’t miss out on the financial freedom you deserve,” “Secure your family’s future today.” These phrases aim to connect with desires and fears rather than providing factual information.
- Threats or Intimidation (less common for income offers, but possible): In some variations, there might be subtle hints of negative consequences for inaction, though this is more typical of phishing attempts for personal data.
Examining the “Loophole” Aspect

In the realm of financial solicitations, the term “loophole” is often wielded like a magic wand, promising effortless gains and tax advantages. However, in the context of Section 5101 bank income email offers, this word frequently serves as a deceptive lure, masking potentially risky or outright fraudulent schemes. Understanding how this term is typically misused is crucial to safeguarding your financial well-being.The allure of a “loophole” suggests a clever exploitation of a gap in rules or laws, often presented as a secret method to achieve favorable outcomes.
In legitimate financial planning, professionals identify and utilize provisions within existing tax codes or financial regulations to optimize outcomes for clients. This is done within the bounds of the law and with transparency. Conversely, offers that sensationalize “loopholes” often imply circumventing established principles or engaging in activities that are, at best, ethically questionable, and at worst, illegal. The language used is designed to evoke a sense of urgency and exclusivity, prompting individuals to act without due diligence.
Misrepresentation and Misuse of the Term “Loophole”
Financial solicitations frequently employ the term “loophole” to imply a hidden or overlooked pathway to significant financial benefits, particularly in tax matters. This term is often employed to create an impression of insider knowledge or a unique advantage that the average person is unaware of. In reality, what is presented as a “loophole” might be a misunderstanding of complex regulations, an aggressive tax avoidance strategy that borders on evasion, or an outright fabrication designed to entice victims into a scam.
The intention is to bypass the conventional and often more arduous processes of legitimate financial growth and tax planning, offering a seemingly shortcut.
Legality and Ethical Implications of Exploiting Perceived Loopholes
The exploration of what are perceived as financial or tax loopholes carries significant legal and ethical weight. Legitimate financial planning involves working within the framework of established laws and regulations, utilizing legal provisions for tax deductions, credits, and other benefits. This is a form of tax avoidance, which is legal. However, the pursuit of “loopholes” as advertised in questionable offers often ventures into the territory of tax evasion, which is illegal.
Tax evasion involves intentionally misrepresenting income, concealing assets, or otherwise failing to pay taxes that are legally owed. Ethically, exploiting loopholes often involves benefiting at the expense of others or undermining the fairness of the financial system.
Legitimate tax avoidance is legal; tax evasion is illegal. The line between the two can be subtle, but the intent to deceive or defraud the government is the defining factor in illegality.
Potential Consequences of Engaging with Offers Promising Loophole Exploitation
Engaging with offers that promise to exploit perceived tax or financial loopholes can lead to severe repercussions. These consequences extend beyond financial penalties and can encompass legal action and reputational damage.
- Financial Penalties: This can include substantial back taxes, accrued interest, and significant fines levied by tax authorities.
- Legal Prosecution: Depending on the severity of the scheme, individuals may face criminal charges for tax fraud or evasion, leading to potential imprisonment.
- Audits and Scrutiny: Participating in such schemes often flags individuals for increased scrutiny from tax agencies, leading to prolonged and invasive audits.
- Loss of Assets: Illegally obtained gains or assets used in fraudulent schemes can be seized by authorities.
- Reputational Damage: A conviction or even an investigation can severely damage one’s personal and professional reputation, impacting future opportunities.
Comparison of Legitimate Financial Planning Strategies with Questionable Offers
A clear distinction exists between sound financial planning and the deceptive promises often found in offers touting “loopholes.” Legitimate strategies are characterized by transparency, adherence to legal frameworks, and a focus on long-term financial health.
| Legitimate Financial Planning | Questionable “Loophole” Offers |
|---|---|
| Focuses on established tax laws, deductions, and credits. | Promises obscure or nonexistent “loopholes” for rapid gains. |
| Employs diversified investment strategies and risk management. | Often relies on a single, high-risk, or unsubstantiated method. |
| Involves qualified professionals (CPAs, CFPs) who are regulated and licensed. | Often promoted by anonymous or unregulated entities. |
| Emphasis on long-term wealth building and security. | Focuses on immediate, unrealistic returns with little regard for sustainability. |
| Requires thorough documentation and compliance with regulations. | Often involves secrecy, avoidance of proper documentation, or misleading financial structures. |
Legitimate financial planning is akin to building a strong house with a solid foundation and following building codes. It is a methodical process that ensures stability and longevity. Conversely, offers that promise to exploit “loopholes” are often like building a house on sand, with the hope of a quick and easy construction, but with the inevitable risk of collapse.
If you’re wondering if that Section 5101 loophole bank income email offer is a scam, it’s wise to be cautious. Understanding basic banking, like knowing how do you fill out a bank deposit slip , is a good first step to financial literacy. Always verify such offers through official channels before proceeding, as many are indeed scams.
The Role of Email in These Offers

In our pursuit of financial wisdom and security, it is crucial to understand the conduits through which tempting, yet potentially perilous, opportunities are presented. Unsolicited emails, often arriving with the promise of extraordinary returns or exclusive access, serve as the primary gateway for many of these “Section 5101 loophole” schemes. These messages are not mere digital correspondences; they are carefully crafted instruments designed to bypass our rational defenses and appeal directly to our aspirations.
Recognizing the architecture and tactics within these emails is akin to understanding the subtle currents of a river before embarking on a journey.These digital missives are more than just words on a screen; they are psychological tools. They leverage the immediacy of the inbox and the allure of the unknown to create a compelling narrative that, unfortunately, often leads to significant financial distress.
By dissecting the typical structure, the urgency-inducing ploys, and the tell-tale sender information, we equip ourselves with the necessary discernment to navigate this often murky digital landscape.
Typical Structure of Unsolicited Financial Opportunity Emails
The unsolicited email, a harbinger of many a financial scheme, typically follows a predictable yet insidious structure, designed to capture attention and elicit a swift, often unthinking, response. The opening gambit is usually a sensational headline or subject line, promising something extraordinary that seems too good to be true – and often, it is. This is followed by a compelling narrative that highlights a supposed secret, a hidden advantage, or an overlooked opportunity.
The body of the email will then elaborate on the supposed benefits, often using vague but impressive-sounding jargon, and present a clear call to action.These emails commonly feature:
- Captivating Subject Lines: Phrases like “URGENT: Access Your Hidden Tax Refund!” or “Exclusive Opportunity: Unlock Section 5101 Savings NOW!” are designed to pique immediate interest and bypass initial skepticism.
- Appealing Opening Statements: The email often begins by addressing a common financial pain point or aspiration, such as “Are you tired of overpaying taxes?” or “Imagine a world where your money works harder for you.”
- Elaboration on the “Secret”: The core of the message explains, in broad strokes, the supposed “loophole” or unique strategy. This explanation is typically devoid of concrete details or verifiable mechanisms, relying instead on buzzwords and promises of massive gains.
- Testimonials and Social Proof (Often Fabricated): Scammers frequently include glowing testimonials from supposed satisfied clients, or mention large sums of money allegedly saved or earned, to build credibility. These are rarely verifiable.
- Urgency and Scarcity Tactics: Phrases like “Limited spots available,” “Offer ends soon,” or “Act within 24 hours” are employed to pressure recipients into making hasty decisions.
- Call to Action: This is usually a request to click a link, download a document, call a specific number, or reply to the email to learn more or “secure your spot.”
Common Tactics for Creating Urgency and Exclusivity
The art of persuasion in scam emails often hinges on manufacturing a sense of immediate need or special privilege. Scammers understand that hesitation is the enemy of their enterprise, and therefore, they employ a range of psychological triggers to bypass critical thinking. These tactics are not subtle; they are designed to overwhelm our natural inclination to investigate and instead foster a reactive mindset.The following tactics are frequently observed:
- Time-Limited Offers: Stating that the opportunity is only available for a short duration, such as “This offer expires at midnight tonight!” or “Only 3 days left to claim your benefit.”
- Limited Availability: Implying that only a select few can participate, for instance, “We are only accepting 50 new clients this month,” or “This is an exclusive invitation for a select group.”
- Fear of Missing Out (FOMO): Highlighting the potential losses or missed gains if the recipient does not act quickly. This can be framed as “Don’t let your neighbors benefit while you miss out” or “The longer you wait, the more money you lose.”
- Personalized (but Generic) Appeals: While the email might address you by name, the content often feels boilerplate, yet it might also imply a unique, personalized advantage is being offered to you specifically, creating a false sense of individual attention.
- “Secret” or “Confidential” Information: Framing the opportunity as something not widely known, thus implying that by acting now, you are gaining access to privileged, insider knowledge.
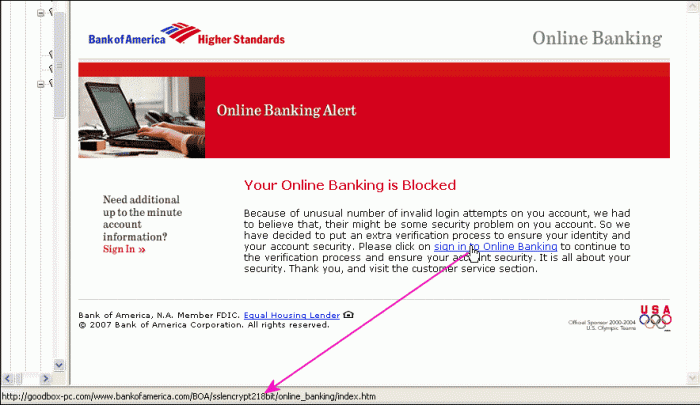
Sender Addresses and Domains Associated with Fraudulent Activity
The origin of an email can often be a significant indicator of its legitimacy. Fraudulent actors, in their pursuit of anonymity and broad reach, tend to utilize sender addresses and domain names that exhibit certain characteristics. Vigilance in scrutinizing these details can serve as an early warning system, preventing engagement with potentially harmful communications.Commonly associated sender details include:
- Free Email Services with Suspicious Names: Emails from providers like Gmail, Yahoo, or Hotmail, but with sender names that are generic, nonsensical, or attempt to mimic official entities (e.g., “[email protected],” “[email protected]”). Official government or financial institutions rarely use these free services for direct unsolicited communication.
- Newly Registered or Unfamiliar Domains: Scammers often create websites and email addresses with domain names that are slightly misspelled versions of legitimate organizations or use obscure, newly registered domain extensions (e.g., .xyz, .top, .info) that are not typically used by reputable financial institutions.
- Domains Mimicking Official Institutions: Be wary of addresses that closely resemble official domains but have slight alterations, such as “irs.gov.scam.com” instead of “irs.gov.”
- Generic or Impersonal Sender Names: While not always indicative of fraud, sender names like “Admin,” “Support,” or simply a string of numbers and letters can be a red flag when combined with other suspicious elements.
- Lack of Professionalism in Domain Names: Official entities usually have well-established and professional-sounding domain names. A domain that appears hastily created or unprofessional is a cause for concern.
Scrutinizing Email Headers and Sender Details for Suspicious Patterns
The seemingly innocuous details of an email’s origin, often hidden within its headers, can reveal a wealth of information about its sender and intent. Learning to examine these elements is a critical skill in discerning legitimate communications from fraudulent ones. It requires a methodical approach, looking for inconsistencies and anomalies that a legitimate sender would not typically exhibit.To effectively scrutinize email headers and sender details:
- Examine the “From” Address Carefully: Look beyond the display name to the actual email address. Is it a free service? Does the domain name look legitimate? Are there any subtle misspellings or unusual characters?
- Check the “Reply-To” Address: Sometimes, the “From” address might appear legitimate, but the “Reply-To” address will be different and often more suspicious. Ensure both match or are consistent with a reputable source.
- Investigate the Sending Server (via Headers): Most email clients allow you to view the original message headers. These headers contain information about the path the email took to reach your inbox, including the originating server. Look for IP addresses that are from unusual geographic locations or belong to known spam-sending networks. Tools like MXToolbox can help analyze IP addresses.
- Analyze the Date and Time Stamps: While less definitive, inconsistencies in timestamps or unusually rapid sending patterns from a supposed official source might be noteworthy.
- Look for Mismatched Domain Authentication: Legitimate organizations often use technologies like SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) to authenticate their emails. If these checks fail or are absent, it can indicate a spoofed email. This information is typically found deep within the headers.
- Cross-Reference Information: If the email claims to be from a specific company or government agency, visit their official website directly (do not use links from the email) and look for contact information or statements about how they communicate with the public.
The digital envelope is as important as the message it carries. Always scrutinize the sender’s credentials with the same rigor you would a physical letter claiming to offer you a fortune.
Financial and Legal Ramifications
The allure of quick financial gains, especially when presented as a clever “loophole,” can often blind individuals to the severe consequences that lie beneath the surface. This section delves into the stark realities of financial and legal repercussions that await those who fall prey to such deceptive offers, emphasizing the critical need for due diligence and professional counsel.These schemes are meticulously designed to exploit trust and a desire for easy money, leading to significant financial erosion and entanglement in legal quagmires.
Understanding these ramifications is not merely an academic exercise but a vital protective measure against becoming another victim.
Potential Financial Losses
Falling for fraudulent financial schemes, such as those promising access to non-existent “bank income loopholes,” can result in devastating financial losses. These losses often extend beyond the initial investment, encompassing hidden fees, subsequent demands for more money, and the complete disappearance of the promised returns, leaving individuals with nothing but empty accounts.The spectrum of financial damage can be illustrated through several common scenarios:
- Irretrievable Investment: The most immediate loss is the principal amount invested, which is often transferred to offshore accounts or dissipated before any recourse can be taken.
- Accumulation of Fees: Scammers frequently introduce a series of escalating “processing fees,” “administrative charges,” or “tax liabilities” that must be paid before any supposed funds can be accessed. These fees are often a significant portion of the initial investment and continue to mount.
- Loss of Future Earnings: Individuals might liquidate legitimate assets or take out loans to fund these schemes, thereby losing potential earnings from those assets or incurring interest payments on debt.
- Identity Theft and Further Fraud: The personal and financial information collected during the fraudulent transaction can be exploited for identity theft, leading to further financial crimes and damages.
- Opportunity Cost: Time and mental energy spent pursuing these phantom opportunities could have been invested in legitimate financial planning, career development, or genuine investment strategies.
Legal Repercussions of Fraudulent Scheme Participation
Engaging with fraudulent financial schemes, even if one believes they are exploiting a “loophole,” can carry significant legal consequences. While the primary perpetrators are subject to criminal prosecution, participants can also face legal challenges, particularly if their actions are deemed complicit or if they knowingly participate in illegal activities.The legal landscape surrounding financial fraud is complex and can lead to:
- Civil Lawsuits: If the scheme involves defrauding others or violating financial regulations, participants might be named in civil lawsuits seeking recovery of lost funds.
- Regulatory Investigations: Financial regulatory bodies may investigate individuals involved in promoting or facilitating such schemes, potentially leading to fines or bans from certain financial activities.
- Criminal Charges: In cases where participants are found to have knowingly engaged in money laundering, tax evasion, or other illegal financial activities as part of the scheme, criminal charges can be filed. This is especially true if the “loophole” involves circumventing legal financial processes.
- Tax Implications: Any purported “income” or “returns” generated from such schemes are often taxable. Failure to report and pay taxes on these gains can lead to penalties and interest from tax authorities. Furthermore, if the scheme itself is designed to evade taxes, participants could be implicated in tax fraud.
Importance of Consulting Qualified Professionals
Navigating the complexities of financial offers, especially those that sound too good to be true, necessitates the guidance of qualified professionals. These experts possess the knowledge and experience to discern legitimate opportunities from fraudulent schemes, protecting individuals from financial ruin and legal entanglements.Seeking professional advice is paramount for several reasons:
- Expert Financial Analysis: Certified Financial Planners (CFPs) or Chartered Financial Analysts (CFAs) can evaluate the viability and risk profile of any investment or financial strategy, comparing it against established financial principles.
- Legal Counsel: Attorneys specializing in financial law or consumer protection can advise on the legality of an offer and the potential legal ramifications of participation. They can identify red flags that might be missed by a layperson.
- Risk Assessment: Professionals can help individuals understand their risk tolerance and align it with realistic financial goals, preventing impulsive decisions driven by speculative offers.
- Fraud Detection: These experts are trained to recognize the patterns and tactics used in financial scams, providing an invaluable layer of defense.
It is imperative to remember that unsolicited financial advice or offers, particularly those found through email, should always be independently verified with trusted professionals.
Questions to Ask Before Considering Unsolicited Financial Offers, Is section 5101 loophole bank income email offer a scam
A structured approach to evaluating any unsolicited financial offer is crucial. Before even entertaining the possibility of engaging with such an offer, a series of critical questions should be posed, both to oneself and to the offeror, to uncover potential deception. This checklist serves as a vital first line of defense.Before proceeding with any unsolicited financial offer, consider the following:
- What is the exact nature of the “loophole” or strategy being offered? (Demand a clear, detailed explanation that is not vague or overly technical.)
- Who is the entity or individual making this offer, and what are their credentials and regulatory standing? (Verify any stated licenses or affiliations.)
- What are the specific risks involved, and how are they mitigated? (Legitimate offers will openly discuss risks; scams often downplay or ignore them.)
- What are the upfront costs, ongoing fees, and any other financial commitments required? (Ensure all costs are transparent and clearly itemized.)
- What is the expected timeline for returns, and what guarantees, if any, are provided? (Be highly skeptical of guaranteed high returns or specific timelines.)
- How will the funds be handled, and what is the process for withdrawal? (Understand the flow of money and the ease of access to your principal.)
- Can I speak with existing clients or receive verifiable testimonials? (Be wary if testimonials are generic or cannot be independently confirmed.)
- Is this offer being presented through official channels, or is it an unsolicited email or social media message? (Unsolicited contact is a significant red flag.)
- Has this offer been vetted by an independent financial advisor or legal counsel? (If not, this is a strong indicator to seek such advice before proceeding.)
- What is the exit strategy, and under what conditions can I retrieve my investment? (Understand how to get your money back, not just how to put it in.)
Protecting Yourself from Scams

In the vast digital expanse, where opportunities and information flow freely, so too do the shadows of deception. Unsolicited financial offers, particularly those promising extraordinary returns through perceived “loopholes,” demand a discerning eye and a robust defense. This section equips you with the knowledge and strategies to navigate these treacherous waters, ensuring your financial well-being remains secure.The digital age has democratized access to information, but it has also amplified the reach of those who seek to exploit it.
Understanding how to identify and thwart these schemes is not merely a matter of financial prudence; it is an act of self-preservation in the online realm.
Verifying the Legitimacy of Financial Offers
When an email arrives with a tantalizing financial proposition, the first and most critical step is to approach it with healthy skepticism. Do not be swayed by immediate promises of wealth; instead, engage in a thorough verification process. This involves cross-referencing information, seeking independent opinions, and understanding the fundamental principles of legitimate financial operations.Here are actionable steps to verify the legitimacy of financial offers received via email:
- Research the Sender: Scrutinize the sender’s email address. Legitimate financial institutions typically use domain names that precisely match their company name (e.g., @bankofamerica.com, not @bankofamerica-support.net). Be wary of generic or misspelled addresses.
- Investigate the Company: Conduct independent searches for the company or individual making the offer. Look for their official website, physical address, and contact information. Check for reviews, news articles, and any regulatory actions filed against them.
- Consult Official Sources: If the offer purports to be from a known financial institution or government agency, visit their official website directly (by typing the URL into your browser, not by clicking a link in the email) or call their publicly listed customer service number to confirm the offer’s existence and details.
- Understand the Product/Service: Ensure you fully comprehend what is being offered. If it sounds too good to be true, it likely is. Legitimate investments and financial products are typically well-documented and their risks clearly articulated.
- Beware of Urgency and Pressure Tactics: Scammers often create a sense of urgency, pressuring you to act quickly before you have time to think or verify. Legitimate offers allow ample time for due diligence.
- Check for Regulatory Registration: For investment opportunities, verify if the entity is registered with relevant financial regulatory bodies in your jurisdiction (e.g., the Securities and Exchange Commission (SEC) in the US, the Financial Conduct Authority (FCA) in the UK).
Reporting Suspicious Email Solicitations
Taking action against fraudulent emails not only protects you but also contributes to the broader effort of combating cybercrime. Reporting these solicitations to the appropriate authorities can help them identify patterns, track down perpetrators, and prevent others from falling victim.Methods for reporting suspicious email solicitations to relevant authorities include:
- Forward to Your Email Provider: Most email services (Gmail, Outlook, Yahoo) have a mechanism to report spam or phishing emails. Look for options like “Report spam,” “Report phishing,” or “Mark as junk” within your email client.
- Report to the Federal Trade Commission (FTC): In the United States, the FTC is the primary agency for collecting scam reports. You can file a complaint online at ReportFraud.ftc.gov.
- Report to the Internet Crime Complaint Center (IC3): Operated by the FBI, IC3 accepts complaints related to a wide range of internet crimes, including phishing and financial fraud. Visit ic3.gov to file a report.
- Contact Your State Attorney General: Many state attorney general offices have consumer protection divisions that handle fraud complaints.
- Report to Financial Regulators: If the scam involves investment fraud, report it to the relevant financial regulatory body in your country or region.
- Report to the Company Being Impersonated: If the scam email impersonates a legitimate company, inform that company directly. They often have dedicated channels for reporting such abuse.
Best Practices for Safeguarding Personal and Financial Information
The security of your personal and financial data is paramount in preventing yourself from becoming a victim of identity theft and financial fraud. Implementing strong security habits online creates a formidable barrier against malicious actors.Elaborating on best practices for safeguarding personal and financial information online:
- Use Strong, Unique Passwords: Avoid using easily guessable passwords or reusing the same password across multiple accounts. Employ a combination of uppercase and lowercase letters, numbers, and symbols. Consider using a reputable password manager to generate and store complex passwords.
- Enable Two-Factor Authentication (2FA): Wherever possible, enable 2FA on your online accounts. This adds an extra layer of security, requiring a second form of verification (e.g., a code sent to your phone) in addition to your password.
- Be Cautious with Public Wi-Fi: Avoid accessing sensitive accounts (banking, shopping) or entering personal information when connected to unsecured public Wi-Fi networks, as these can be vulnerable to interception.
- Regularly Monitor Financial Accounts: Review your bank and credit card statements frequently for any unauthorized transactions. Set up alerts for account activity if your financial institution offers them.
- Shred Sensitive Documents: Before discarding any documents containing personal or financial information, shred them to prevent them from falling into the wrong hands.
- Be Wary of Phishing Attempts: Never click on suspicious links or download attachments from unknown senders. Always verify the sender’s identity through a separate communication channel if you are unsure.
- Keep Software Updated: Ensure your operating system, web browser, and antivirus software are always up-to-date. Updates often include critical security patches that protect against known vulnerabilities.
Personal Strategy for Evaluating Unsolicited Financial Advice or Opportunities
Developing a personal framework for assessing unsolicited financial opportunities is crucial for maintaining financial discipline and avoiding impulsive decisions driven by perceived windfalls. This strategy should be rooted in critical thinking and a deep understanding of your own financial goals and risk tolerance.A robust personal strategy for evaluating unsolicited financial advice or opportunities involves the following components:
- Define Your Financial Goals and Risk Tolerance: Before considering any new financial opportunity, clearly understand your short-term and long-term financial objectives, as well as the level of risk you are comfortable taking. Legitimate opportunities should align with these parameters.
- The “If It Sounds Too Good To Be True” Rule: This adage is a fundamental cornerstone. If an offer promises guaranteed high returns with little to no risk, or claims to exploit a secret “loophole,” it is almost certainly a scam. Real investments involve inherent risks, and returns are not guaranteed.
- Seek Multiple Independent Opinions: Do not rely on the information provided by the unsolicited source alone. Consult with trusted, independent financial advisors, accountants, or legal professionals who have no vested interest in the opportunity.
- Demand Transparency and Documentation: Legitimate financial offers will come with clear, detailed documentation, including prospectuses, terms and conditions, and disclosure statements. Be wary of vague explanations or a reluctance to provide written information.
- Verify Credentials and Affiliations: Thoroughly research the individuals or companies presenting the opportunity. Check for professional licenses, certifications, and any disciplinary actions from regulatory bodies.
- Understand the Exit Strategy and Liquidity: If you invest, how easily can you access your funds if needed? Scammers often tie up your money in complex or illiquid arrangements.
- Trust Your Intuition: While not a substitute for due diligence, your gut feeling can be an important indicator. If something feels off or makes you uncomfortable, it is wise to disengage.
Conclusion

In conclusion, the pervasive nature of deceptive financial offers via email necessitates a vigilant and informed approach. By recognizing the common red flags, understanding the deceptive exploitation of terms like “loophole,” and scrutinizing the communication channels, individuals can significantly mitigate their risk of falling victim to these scams. Prioritizing due diligence, seeking professional advice, and safeguarding personal information are paramount in navigating the complex landscape of financial solicitations and ensuring one’s financial well-being.
FAQ
What is Section 5101 in the context of these email offers?
Section 5101 of the Internal Revenue Code pertains to the collection of taxes. In the context of these scam offers, it is often misrepresented or entirely fabricated as a basis for a supposed financial “loophole” that allows for the generation of untaxed income or significant tax refunds. Legitimate financial planning rarely, if ever, relies on such obscure or misrepresented code sections for broad income generation.
Are there any legitimate ways to leverage bank income or tax loopholes?
Legitimate financial strategies exist for optimizing income and tax liabilities, but these are typically complex, involve significant planning, and are executed through established financial institutions or with qualified tax professionals. They do not involve unsolicited email offers promising quick, easy money through misrepresented code sections. True financial planning focuses on legal deductions, credits, and investment strategies, not on exploiting non-existent loopholes.
What are the typical consequences of engaging with these offers?
Consequences can range from financial loss through fees or investments in fraudulent schemes to legal repercussions if the activities are deemed illegal. Individuals may also face penalties from tax authorities if they attempt to claim benefits based on fraudulent information provided by these scams. Furthermore, providing personal information can lead to identity theft.
How can I verify if a financial offer is legitimate before responding?
Thoroughly research the company or individual making the offer. Look for established credentials, physical addresses, and verifiable contact information. Consult with independent financial advisors or tax professionals to validate any claims. Be wary of any offer that sounds too good to be true, pressures you for immediate action, or requests upfront fees or sensitive personal information without clear justification.
What should I do if I suspect an email offer is a scam?
Do not click on any links, download any attachments, or reply to the email. Report the suspicious email to your email provider and to relevant authorities such as the Federal Trade Commission (FTC) or the Internet Crime Complaint Center (IC3). You can also forward the email to the financial institution or government agency that the scammer is impersonating, if applicable.




